Latest News:
Tipping the odds in your firm’s favour

Take the right steps and precautions to ensure the odds of being attacked are in your favour and save yourself a world of trouble.
When it comes to security, every firm can come across a variety of cyber-attacks, but one of the most damaging attacks seen within the legal industry, especially for SME firms are phishing attacks. This is because the simple, yet effective nature of the attack means that only one slip up is needed for a successful hit on the firm and the damages can be extremely severe, from losing confidential client data to spending a fortune on recovery costs.
Remember, most cyber security hackers are not criminal masterminds, more often than not they are opportunists who hope to be in the right place at the right time – so don’t present them with that opportunity.
With lockdown lifting for all and a mixture of home and office work taking place, inconsistent environments can lead to mistakes. Perhaps now is the time to refresh your mind and go over the subtle phishing tactics used.
What to look out for
Email and website spoofing

Email spoofing can occur once a hacker uses a ‘trusted’ email account from a reputable organisation or similar account by adopting minimal changes that can make it very easily missed by the recipient. This kind of phishing bait can be potentially very harmful to either the individual or to the firm itself, as people can mistake the source as legitimate and provide the hacker with personal, confidential or financial information.
Malicious links and attachments
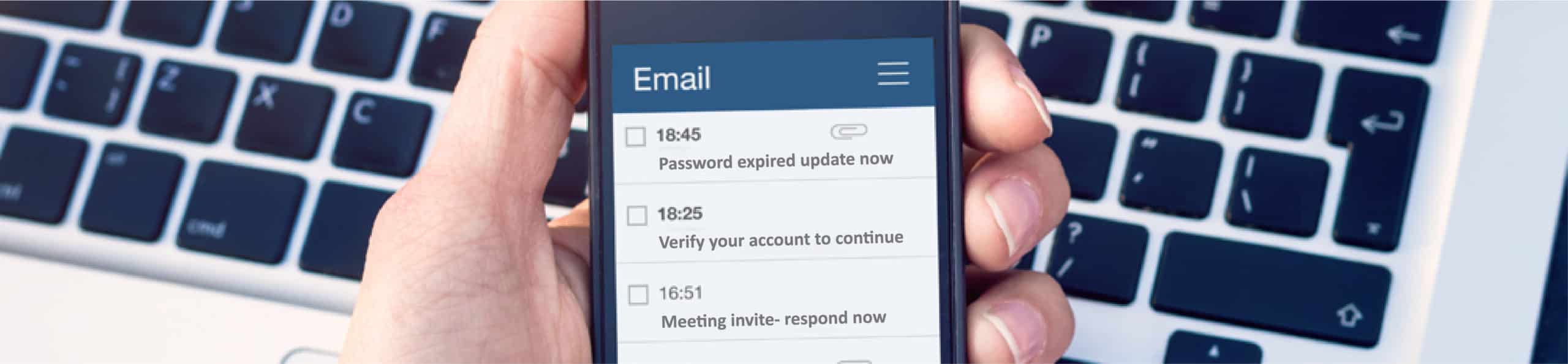
This method aims to lure users into clicking on malicious links and attachments by using ‘trusted’ sources and false pretences such as requiring you to change a password or verify an account. This form of phishing can cause devastating results as the links used contain malware or such similar that can be used for financial gain or redirect users to a page that can retrieve important information by hoodwinking the recipient. Not only can malicious links and attachments be sent through email, but they can also be sent via mobile phones, which is why providing your team with device encryption plus frequent simulation and penetration testing is important to ensure that they are aware of these sophisticated phishing techniques.
Identity forgery

We should all know to be wary of emails with little personalisation, however, it is important to note that phishing is becoming more sophisticated. Identity forgery is a commonly used method for a more targeted approach in phishing attacks. The hacker will use a more familiar and well-informed tone of voice, possibly by imitating a trusted colleague or by customising the email to each target by including the person’s name, which can lead the target to gain some form of trust sometimes referred to as ‘a man in the middle attack’. Be sure to check out for red flags such as either your name or the senders name not being spelt correctly, the email address not matching the name, or an unfamiliar link attached. If in doubt, contact the person the email is sent from on another source to verify it was them who sent the email.
