Latest News:
5 methods used by hackers to get into your firm’s IT systems

Helping your firm avoid the phishing bait.
The holidays are approaching and as everyone prepares to unwind for the much-needed time off, hackers all over the world are just getting started. The Holiday period is likely to bring in a huge increase in the number of phishing attacks and as your team deals with last minute jobs and hectic schedules it becomes more likely that the hacker’s scams and tricks could slip through your security cracks.
Help your firm avoid the bait and look at the 5 common methods used by hackers to get into your firm’s IT systems.
1. Email and website spoofing

Email spoofing can occur once a hacker uses a ‘trusted’ email account from a reputable organisation or similar account by adopting minimal changes that can make it very easily missed by the recipient. This kind of phishing bait can be potentially very harmful to either the individual or to the firm itself, as people can mistake the source as legitimate and provide the hacker with personal, confidential or financial information.
2. Malicious links and attachments
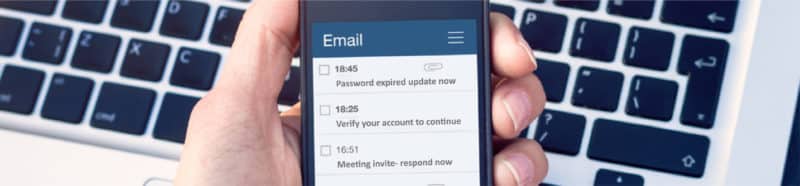
This method aims to lure users into clicking on malicious links and attachments by using ‘trusted’ sources and false pretences such as requiring you to change a password or verify an account. This form of phishing can cause devastating results as the links used contain malware or such similar that can be used for financial gain or redirect users to a page that can retrieve important information by hoodwinking the recipient. Not only can malicious links and attachments be sent through email, but they can also be sent via mobile phones, which is why providing your team with device encryption plus frequent simulation and penetration testing in order to ensure that they are aware of these sophisticated phishing techniques is important.
3. Urgent subjects and calls to action

Hackers know how to stop a person in their tracks, and one sure way of doing this is by adding a sense of urgency to the email, either by attaching a high importance note onto the email, using an engaging subject line that includes a consequence if it is not acted on or adding a call to action at the end of the email followed by a timeframe. This can easily catch a busy solicitor or fee earner off guard and make them react to an email in a hurry without considering the legitimacy of the source.
4. Identity forgery

We should all know to be wary of emails with little personalisation, however, it is important to note that phishing is becoming more sophisticated. Identity forgery is a commonly used method for a more targeted approach in phishing attacks. The hacker will use a more familiar and well-informed tone of voice, possibly by imitating a trusted colleague or by customising the email to each target by including the person’s name, which can lead the target to gain some form of trust sometimes referred to as ‘a man in the middle attack’. Be sure to check out for red flags such as either your name or the senders name not being spelt correctly, the email address not matching the name, or an unfamiliar link attached. If in doubt, contact the person the email is sent from on another source to verify it was them who sent the email.
5. Deals that are too good to be true
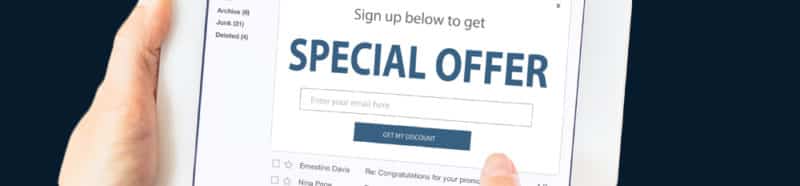
When something sounds too good to be true, the chances are it probably is. Be on the lookout for emails that come out of the blue and offer more than seems possible, especially when they push for a quick financial commitment or ask for personal details. Always check the source of the email and ensure the contact details are ones you can trust.
Spotting the signs for a phishing attack is the first step, adding multiple layers of cyber security defence is the next. There are various ways to prevent and quickly respond to the cyber criminals trying to access your firm’s personal data, from device encryption to mail protection, penetration testing and many more. Explore your options now, leaving it too late will lead to disastrous results that could be avoided.
